When I first built my compact HomeLab around the Morefine M10S Mini PC, I focused on performance, virtualization, and storage efficiency. But as the architecture matured, I realized that true resilience comes from a robust cybersecurity and networking foundation. In this post, I’ll walk through the layered security protocols, authentication mechanisms, and network architecture that protect my HomeLab—designed not just for uptime, but for peace of mind.
Whether you’re looking for hands-on cybersecurity talent, this setup reflects my ability to design, implement, and maintain secure systems in real-world environments.
Recap: The Hardware That Started It All

At the heart of my HomeLab is the Morefine M10S Mini PC—a fanless, low-power unit with four NVMe slots and enough horsepower to run Docker containers, virtual machines, and edge services. With ZimaOS installed on the internal MMC and a RAID 5 array named homenas, I’ve built a modular, energy-efficient system that’s always on and always evolving.
But hardware is only half the story. Let’s talk about how I secured it.
Layered Cyber-security Architecture
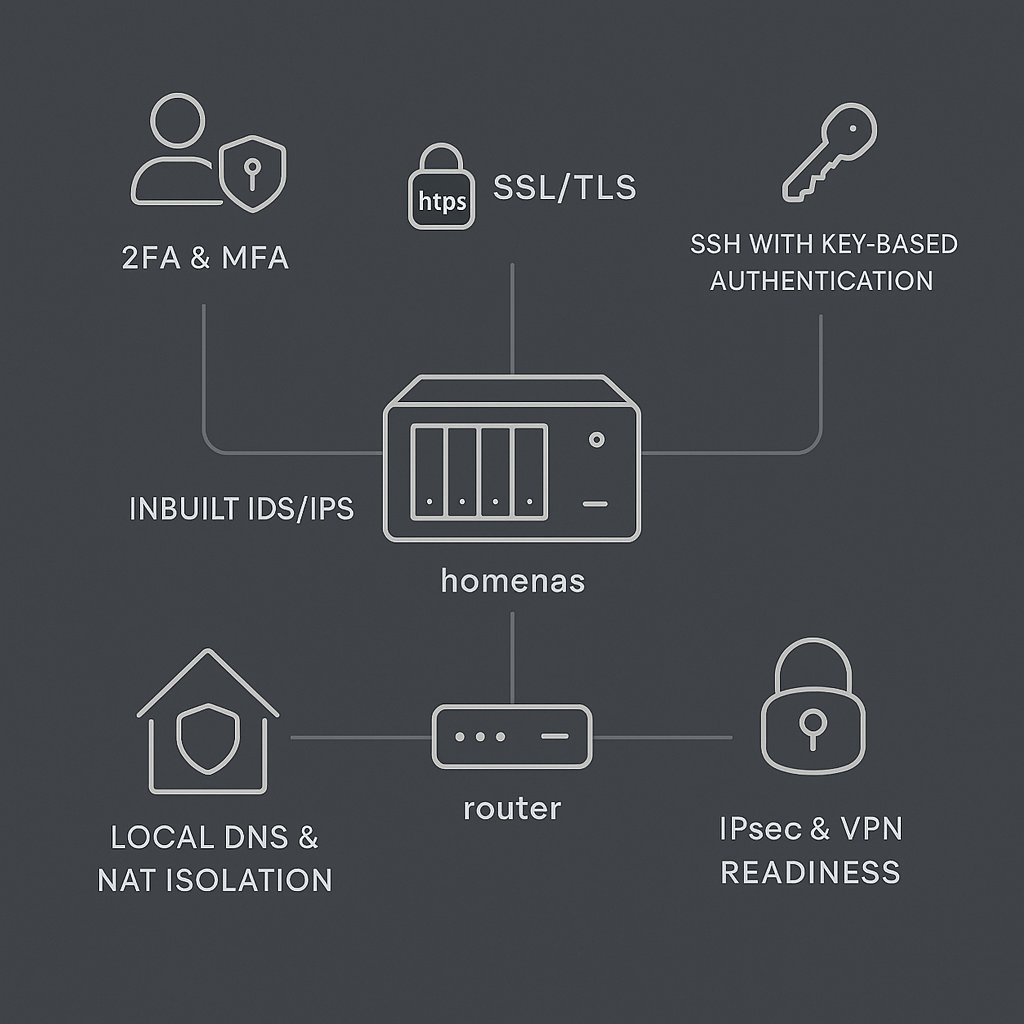
Security in my HomeLab is not a single feature—it’s a philosophy. I’ve implemented a multi-layered defense strategy that combines enterprise-grade tools with open-source flexibility.
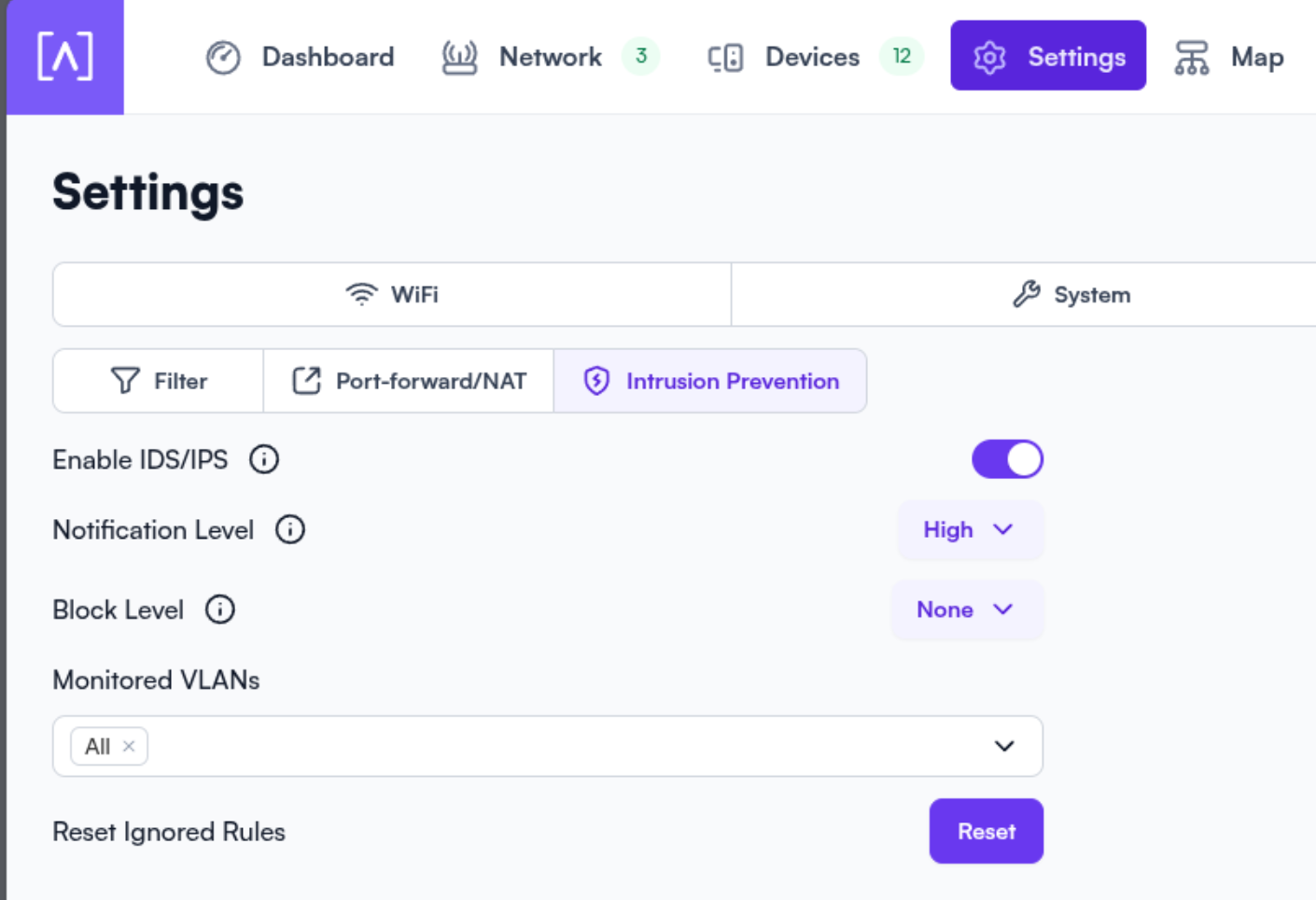
1. Altalabs SDN-Powered IDS/IPS
My Altalabs Route10 router and PoE switch form the backbone of my network. What sets them apart is their built-in Intrusion Detection and Prevention System (IDS/IPS), powered by Software Defined Networking (SDN). This allows dynamic traffic inspection, anomaly detection, and real-time threat mitigation—without needing a separate appliance or VM.
- Traffic Insights: Deep packet inspection and flow analysis
- Threat Response: Automatic blocking of known malicious IPs
- Policy Enforcement: Custom firewall rules and VLAN segmentation
This setup ensures that threats are intercepted before they reach my containers or VMs.
2. Zero Trust Remote Access with Twingate
Instead of exposing ports to the public internet, I use Twingate to implement a zero-trust access model. Only authenticated users can reach internal services, and every connection is encrypted and verified.
- Aliases:
family.pics:[port]→ Immich,family.docs:[port]→ Paperless - DNS Mapping: Local DNS resolves aliases to internal IPs
- WAN Isolation: Only the Twingate connector has WAN access
This architecture ensures that homenas remains private, even when accessed remotely.
3. Authentication Protocols
I’ve enforced strong authentication across all services:
| Protocol | Purpose | Implementation |
|---|---|---|
| 2FA/MFA | Prevent unauthorized access | Enabled on admin portals and remote access |
| SSH Key-Based Auth | Secure shell access | Password logins disabled; keys only |
| OAuth 2.0 | Third-party app integration | Used for select services |
| SSL/TLS | Encrypt web traffic | All services run behind HTTPS |
These protocols ensure that even if credentials are compromised, attackers can’t gain access without the second factor.
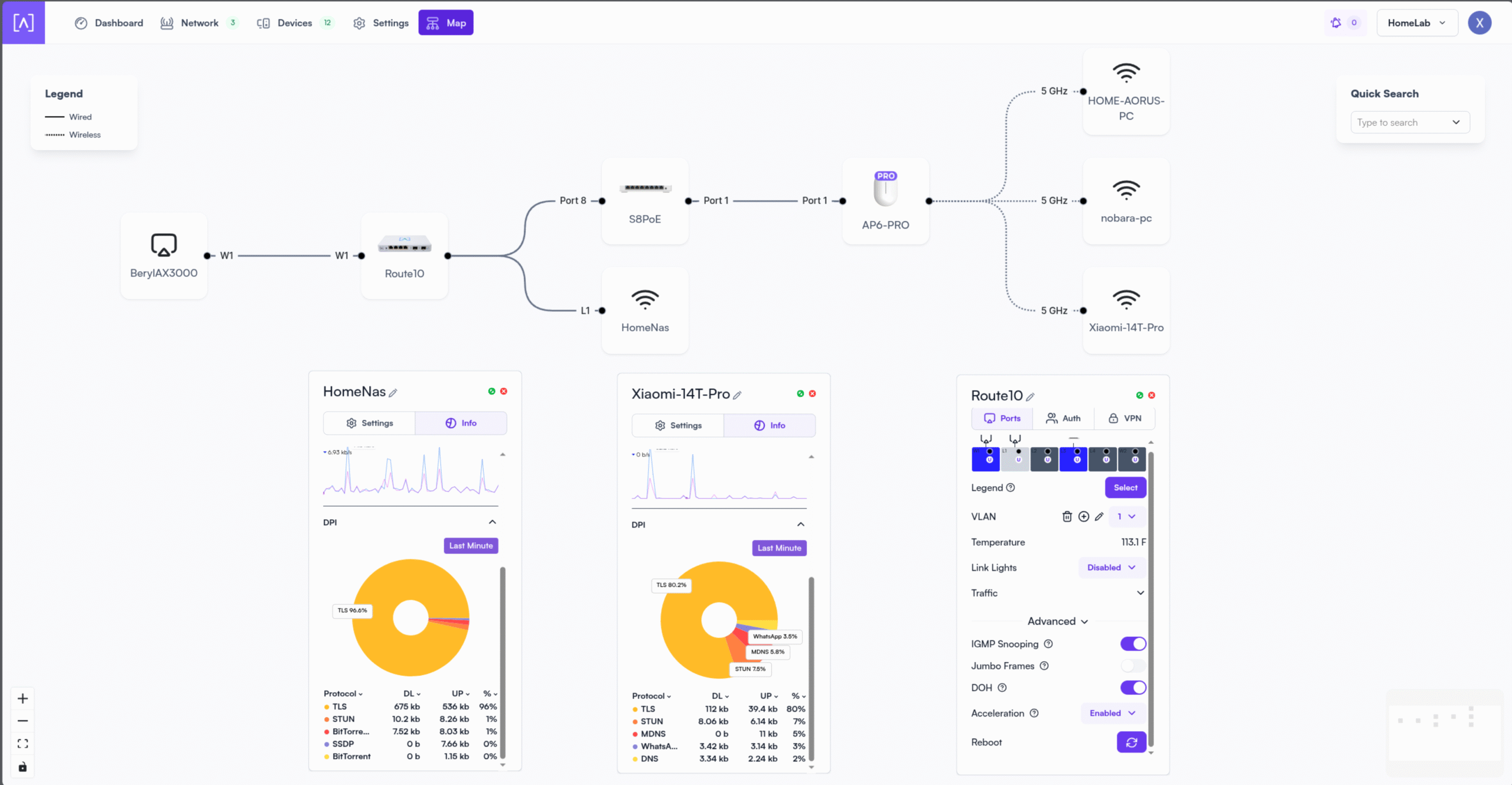
Network Segmentation & DNS Control
A secure network is a segmented network. Here’s how I’ve structured mine:
- Static IP Reservations: ZimaOS and homenas have fixed IPs for consistency
- Local DNS: Internal services are mapped to friendly aliases
- Firewall Rules: LAN-only access for all services except Twingate
- NAT Isolation: Internal IPs are hidden from the public internet
This segmentation minimizes the attack surface and simplifies access control.
Monitoring & Logging
Visibility is key to security. I’ve implemented lightweight monitoring tools to track uptime, resource usage, and container health. Logs from Altalabs and ZimaOS are forwarded to a centralized dashboard for analysis.
- Syslog Integration: Router and OS logs aggregated
- Container Health Checks: Automated alerts for downtime
This gives me real-time insights into system behavior and potential threats.
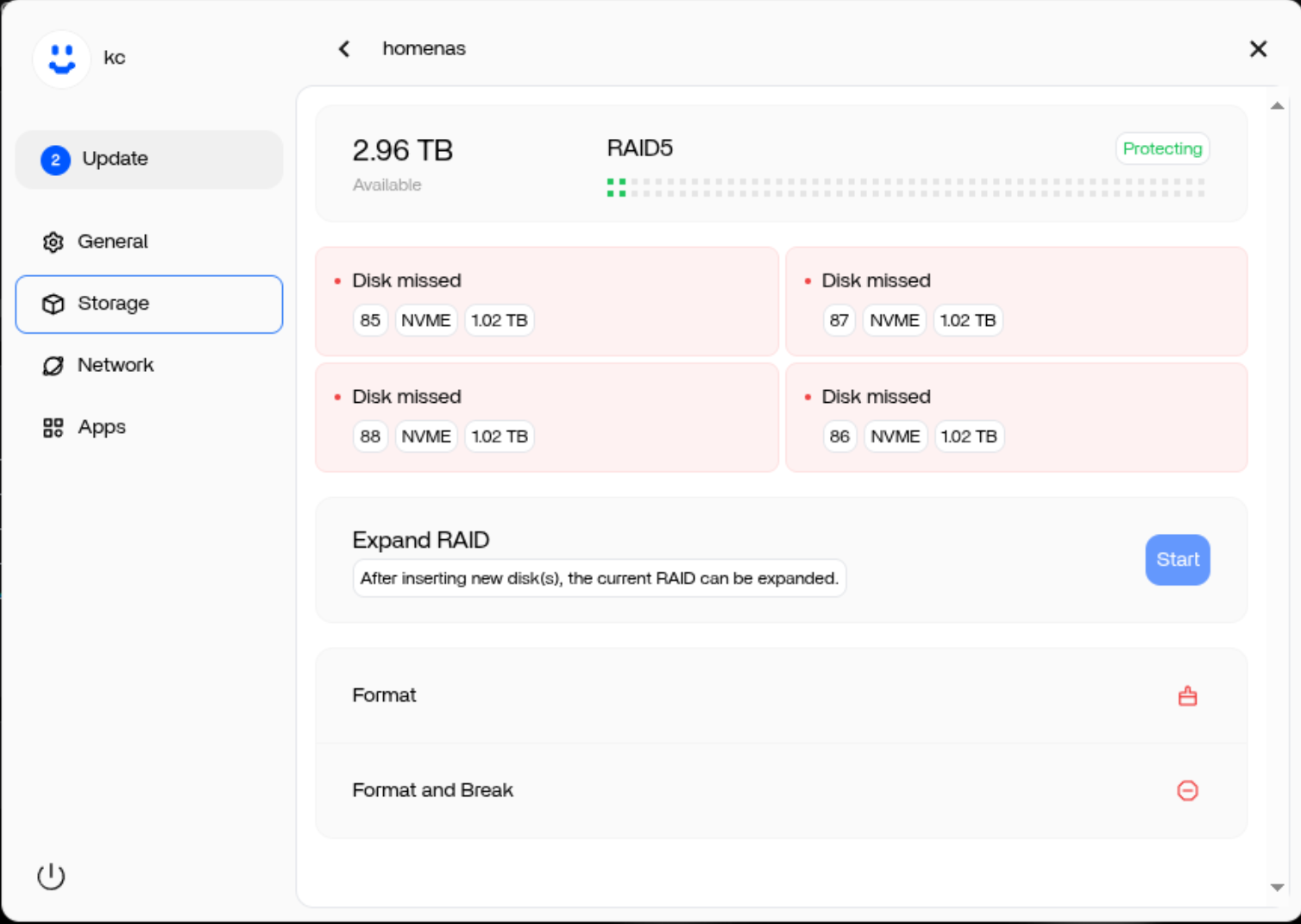
Backup & Recovery Strategy
Security isn’t just about prevention—it’s also about recovery. My RAID 5 array provides redundancy against single-drive failure, and I’ve scheduled automated backups for critical data.
- RAID 5: ~3TB usable space with fault tolerance
- Docker Volume Backups: Nightly snapshots of app data
- VM Snapshots: Periodic backups of virtual machines
This ensures that I can recover quickly from hardware failures or data corruption.
Why This Matters
This HomeLab isn’t just a personal project—it’s a living portfolio. It demonstrates:
- Hands-on experience with software-defined networks (SDN), IDS/IPS, and zero-trust architecture
- Practical knowledge of authentication protocols and encryption standards
- Ability to design resilient systems with redundancy and recovery in mind
- Adaptability to new tools, platforms, and security paradigms
In a world where cybersecurity threats evolve daily, I’ve built a system that’s not only functional—but fortified.
Final Thoughts
My HomeLab began as a compact server build. Today, it’s a secure, scalable, and intelligent system that reflects my curiosity, creativity, and commitment to best practices in cybersecurity and networking.
Whether I’m spinning up a new VM, deploying a containerized app, or analyzing traffic logs, I’m constantly learning—and applying that knowledge to build systems that are both powerful and secure.
If you’re looking for someone who blends technical depth with hands-on execution, I invite you to explore my work. This isn’t just a lab—it’s a launchpad.